Discover a complete picture of your attack surface.
Because you can’t protect what you don’t know about.
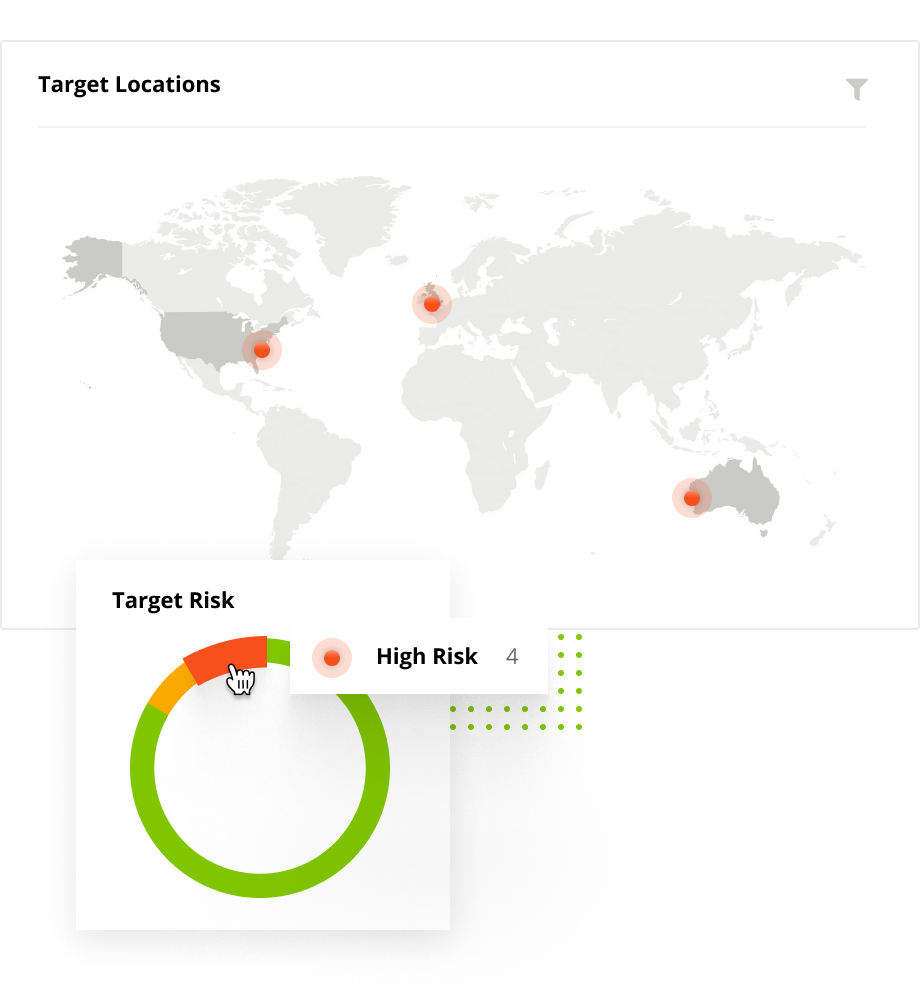
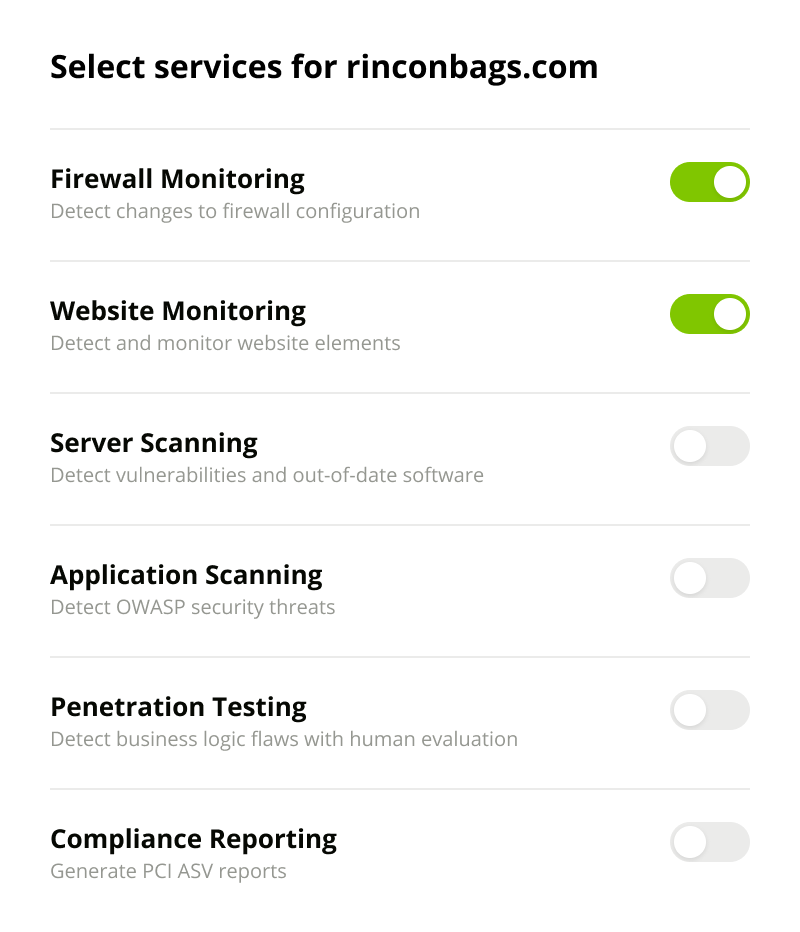
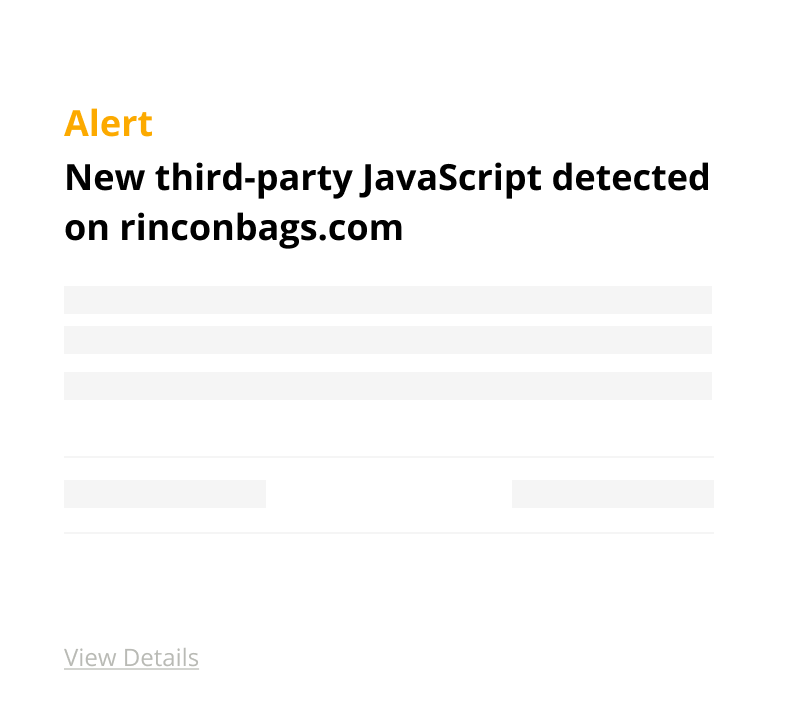
Modern business moves fast. Developers add new websites, services and software. Old assets are forgotten and new acquisitions are brought into the fold. Every website, server, certificate or third-party JavaScript creates another way in for attackers looking to steal customer data.
Our agentless and recursive discovery engine discovers the assets you’re not aware of, so you can prioritize your efforts from a single pane-of-glass.
Learn more about Attack Surface Discovery →